- TechOps Examples
- Posts
- Understanding AWS VPC Flow Logs
Understanding AWS VPC Flow Logs
TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities and articles.
👋 Before we begin... a big thank you to today's sponsor HUBSPOT
Want to get the most out of ChatGPT?
ChatGPT is a superpower if you know how to use it correctly.
Discover how HubSpot's guide to AI can elevate both your productivity and creativity to get more things done.
Learn to automate tasks, enhance decision-making, and foster innovation with the power of AI.
If you’re not a subscriber, here’s what you missed last week.
To receive all the full articles and support TechOps Examples, consider subscribing:
Daily News for Curious Minds
Be the smartest person in the room by reading 1440! Dive into 1440, where 4 million Americans find their daily, fact-based news fix. We navigate through 100+ sources to deliver a comprehensive roundup from every corner of the internet – politics, global events, business, and culture, all in a quick, 5-minute newsletter. It's completely free and devoid of bias or political influence, ensuring you get the facts straight. Subscribe to 1440 today.
IN TODAY'S EDITION
🧠 Use Case
Understanding AWS VPC Flow Logs
🚀 Top News
👀 Remote Jobs
Verana Health is hiring a DevOps Engineer
Remote Location: Worldwide
Halcyon is hiring a Cloud Observability and Performance Engineer
Remote Location: Worldwide
📚️ Resources
🧠 USE CASE
Understanding AWS VPC Flow Logs
VPC Flow Logs capture IP traffic going to and from network interfaces in your VPC. These logs help you understand network behavior, troubleshoot connectivity issues, and monitor for suspicious activity.

VPC Flow log Breakdown
A typical VPC Flow Log infers:
Who initiated the connection: Source IP and port (srcaddr, srcport)
Who received it: Destination IP and port (dstaddr, dstport)
What kind of traffic it was: Protocol such as TCP (6)
How much traffic flowed: Packets and bytes
When it happened: Start and end timestamps
Whether it was allowed or blocked: action (ACCEPT or REJECT)
If logging succeeded: status (OK or error)
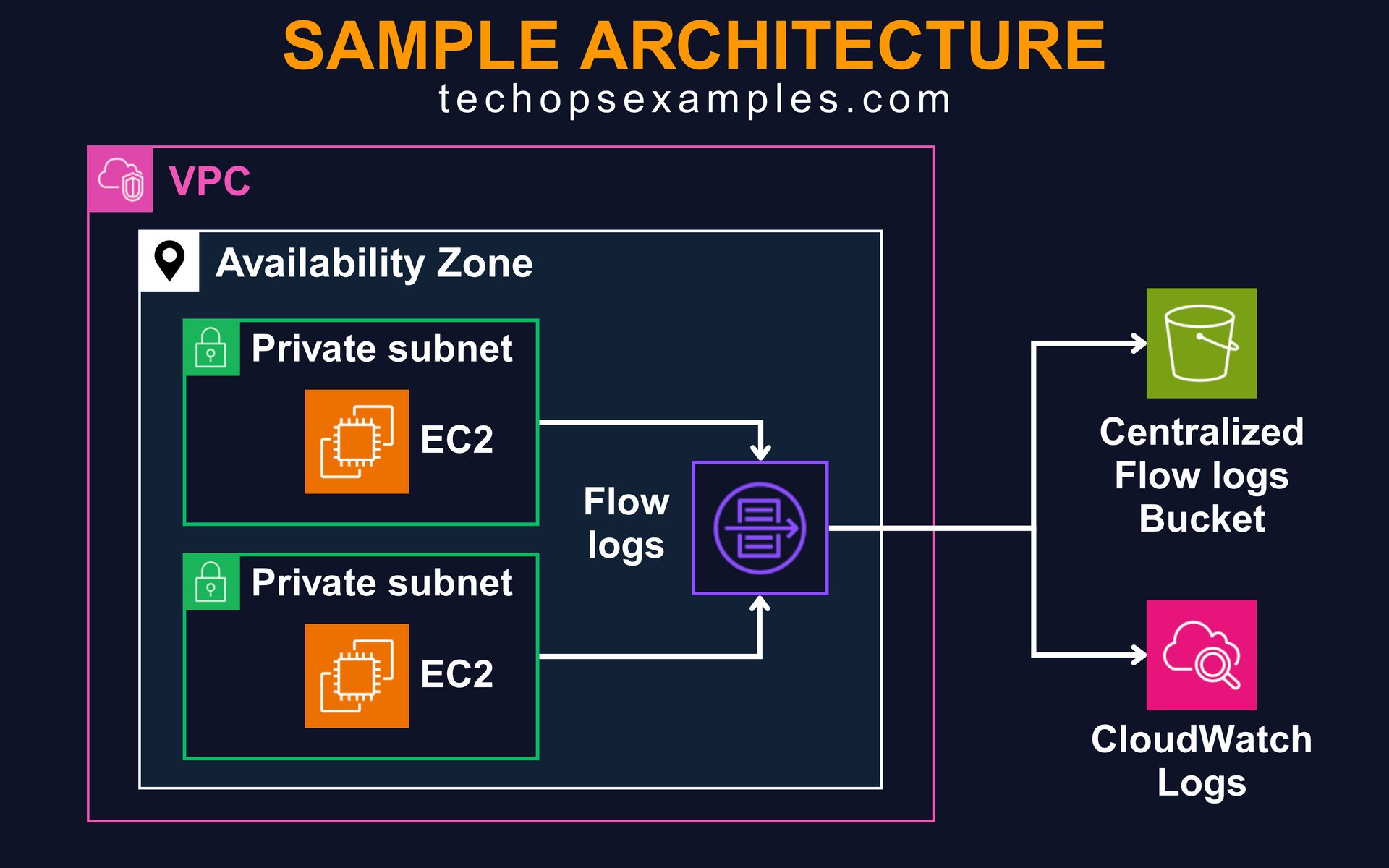
In real world environments, VPC Flow Logs are often enabled at the subnet or VPC level to monitor traffic across critical infra. Teams forward logs to a centralized S3 bucket for long term retention and to CloudWatch Logs for real time alerting and investigations. This setup helps security teams detect suspicious connections, investigate denied traffic, and validate firewall rules. It also supports compliance audits by providing a clear trail of all accepted and rejected network flows within the VPC.
Real World Scenarios Using VPC Flow Logs
1. EC2 Instance Not Reachable via SSH
You launch a new EC2 instance but cannot SSH into it. Flow logs show no entries from your IP, which means traffic is not reaching the instance, likely due to a missing inbound rule or incorrect routing.
Action: Check the security group for port 22 access, verify route table and NACLs, and confirm public IP assignment.
2. Unexpected Data Transfer
You notice a spike in AWS data transfer costs. Flow logs show a specific EC2 instance sending large volumes of outbound traffic to an unknown IP. Possible data exfiltration or misconfigured process.
Action: Quarantine the instance, investigate the process, and block the external IP at the network layer.
3. Connectivity Debugging
Internal users report intermittent timeouts when accessing an internal API. Flow logs show ACCEPT entries but with unusually low packet counts. Connections are accepted but not completing, possibly due to app timeouts or dropped responses.
Action: Check application logs, inspect client behavior, and correlate with flow log timestamps.


