- TechOps Examples
- Posts
- Understanding AWS VPC Peering Configurations
Understanding AWS VPC Peering Configurations
TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities, and articles.
👋 Before we begin... a big thank you to today's sponsor FINTECH TAKES
If you work in fintech or finance, you already have too many tabs open and not enough time.
Fintech Takes is the free newsletter senior leaders actually read. Each week, we break down the trends, deals, and regulatory moves shaping the industry — and explain why they matter — in plain English.
No filler, no PR spin, and no “insights” you already saw on LinkedIn eight times this week. Just clear analysis and the occasional bad joke to make it go down easier.
Get context you can actually use. Subscribe free and see what’s coming before everyone else.
👀 Remote Jobs
Ready is hiring a DevOps Engineer
Remote Location: Worldwide
Iodine is hiring a Site Reliability Engineer - AWS
Remote Location: Worldwide
📚️ Resources
🔴 Get my DevOps & Kubernetes ebooks! (free for Premium Club and Personal Tier newsletter subscribers)
Looking to promote your company, product, service, or event to 52,000+ Cloud Native Professionals? Let's work together. Advertise With Us
🧠 DEEP DIVE USE CASE
Understanding AWS VPC Peering Configurations
In AWS, VPC Peering is a networking connection that lets two VPCs communicate using private IP addresses. Instances in either VPC can exchange traffic directly without internet gateways, VPNs, or Transit Gateway.
When Typically VPC Peering is Needed
Establishing connectivity across AWS accounts.
Enabling inter region communication between VPCs.
Routing of traffic between VPCs without using the internet.
Sharing resources such as databases or services across VPCs.
What Happens Internally
When a VPC Peering connection is created, AWS establishes a direct network link between the requester and accepter VPCs. Communication depends on routing and security configuration.
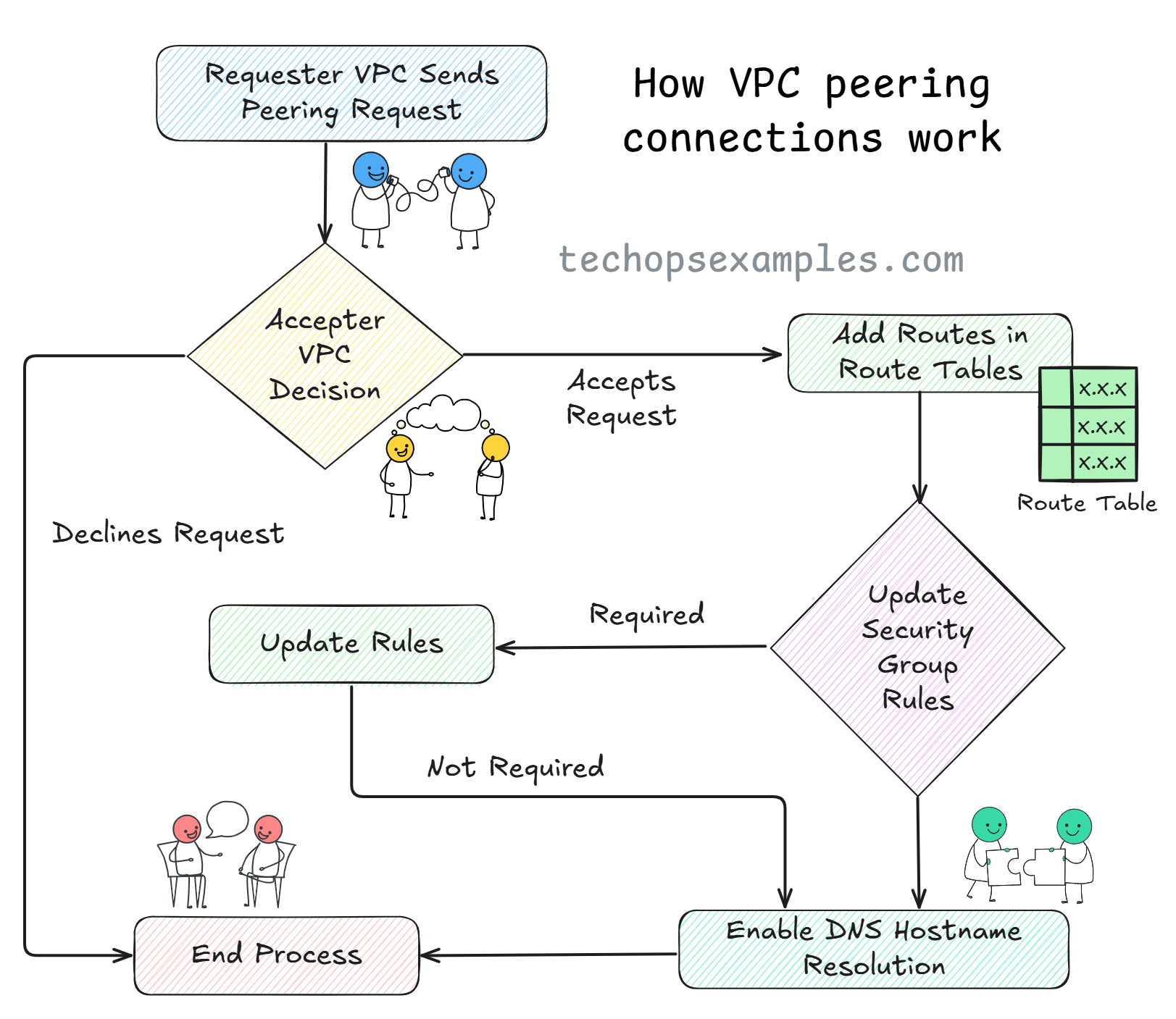
A peering connection ID is created and must be accepted by the target VPC.
Each VPC must update its route tables to include the CIDR block of the peer VPC.
Security groups and network ACLs must explicitly allow traffic to and from the peer VPC.
DNS settings can be enabled so private hostnames in one VPC resolve to private IPs in the peer VPC.
Typically you can configure VPC peering in many ways:
A simple VPC peering configuration with routes to an entire VPC with two VPCs looks like this. VPC A and VPC B are peered, and route tables in both VPCs include the full CIDR block of the peer.

What This Means
Instances in VPC A can send traffic to any instance in VPC B, and vice versa.
All subnets of both VPCs are reachable without defining subnet level routes.
Security groups and NACLs still control which traffic is allowed.
Use Cases
Centralized services such as logging or monitoring accessible from all VPCs.
Applications split across two VPCs that require unrestricted connectivity.
Simplified routing where subnet isolation is not required.
Full CIDR peering makes every subnet routable across VPCs. Restrict access with security groups if only specific resources should communicate.
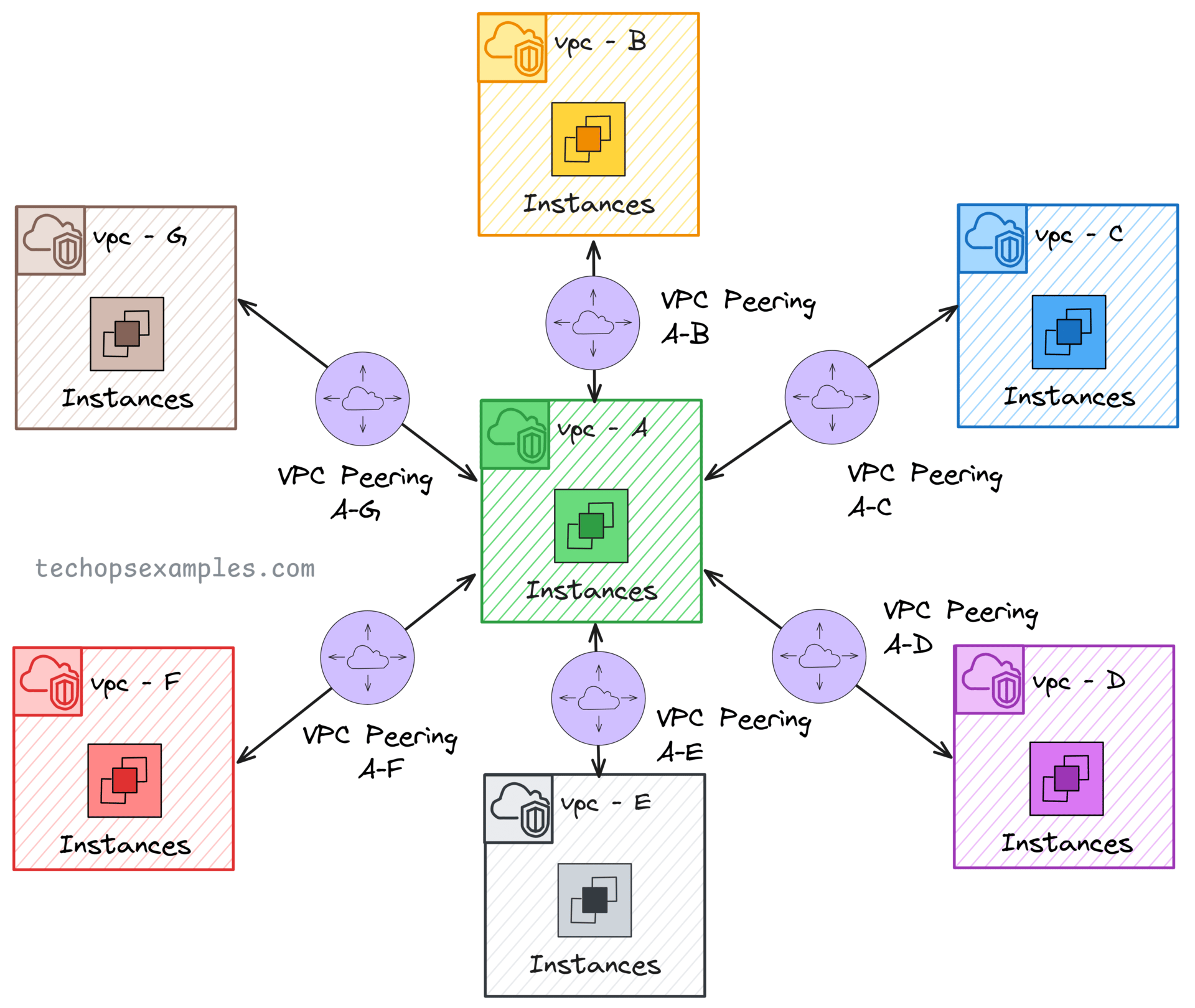
VPC peering follows a full mesh architecture, meaning every VPC must have a direct peering connection with every other VPC it needs to communicate with.

In this Example:
VPC A ↔ VPC B (Peered)
VPC B ↔ VPC C (Peered)
VPC A ↔ VPC C (Peered)
Notice that even though A is connected to B, and B is connected to C, traffic cannot flow from A to C through B. If you need A to talk to C, you must set up a separate peering connection.
You can build the same with multiple VPCs as your network grows, creating a larger mesh of peering connections to scale the architecture.
A VPC peering configuration with specific routes connects VPCs but limits communication only to selected subnets. Instead of adding the full peer CIDR, the route tables are updated with entries pointing only to the required prefixes.

I am giving away 25% OFF on all annual plans of membership offerings.
A membership will unlock access to read these deep dive editions on Thursdays and Saturdays.

Upgrade to Paid to read the rest.
Become a paying subscriber to get access to this post and other subscriber-only content.
Already a paying subscriber? Sign In.
Paid subscriptions get you:
- • Access to archive of 200+ use cases
- • Deep Dive use case editions (Thursdays and Saturdays)
- • Access to Private Discord Community
- • Invitations to monthly Zoom calls for use case discussions and industry leaders meetups
- • Quarterly 1:1 'Ask Me Anything' power session

