TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities, and articles.
👋 👋 A big thank you to today's sponsor WISPR FLOW
Vibe code with your voice
Vibe code by voice. Wispr Flow lets you dictate prompts, PRDs, bug reproductions, and code review notes directly in Cursor, Warp, or your editor of choice. Speak instructions and Flow will auto-tag file names, preserve variable names and inline identifiers, and format lists and steps for immediate pasting into GitHub, Jira, or Docs. That means less retyping, fewer copy and paste errors, and faster triage. Use voice to dictate prompts and directions inside Cursor or Warp and get developer-ready text with file name recognition and variable recognition built in. For deeper context and examples, see our Vibe Coding article on wisprflow.ai. Try Wispr Flow for engineers.
👀 Remote Jobs
PostHog is hiring a Platform Engineer
Remote Location: Worldwide
Sleek is hiring a Principal SRE Engineer
Remote Location: India, Singapore, Australia, Vietnam, Philippines
📚 Resources
Looking to promote your company, product, service, or event to 58,000+ Cloud Native Professionals? Let's work together. Advertise With Us
🧠 DEEP DIVE USE CASE
How to Implement Security Guardrails in AKS Deployments
Before implementing security guardrails in AKS, it is important to understand how the operational and security responsibility model changes when compared to self managed Kubernetes deployments.
Self managed Kubernetes responsibility model
In a self managed Kubernetes setup, the cluster is a closed system.
You operate the control plane. You own the worker nodes. You decide how workloads are executed. Everything runs inside infrastructure you manage directly.

From a security standpoint, this means
The control plane is part of your attack surface
etcd exposure is your risk
API server hardening is your responsibility
Worker nodes are long lived and trusted
Pods can only run where you allow them to run
If something is misconfigured, there is no abstraction layer protecting you.
This model offers maximum flexibility but also carries the highest operational and security overhead. Any misconfiguration directly increases risk.
AKS breaks the single boundary model
AKS introduces a managed control plane and multiple execution paths. The Kubernetes API server is still the entry point, but it is no longer part of your infrastructure. Azure owns it. Patches it. Scales it. Protects it.
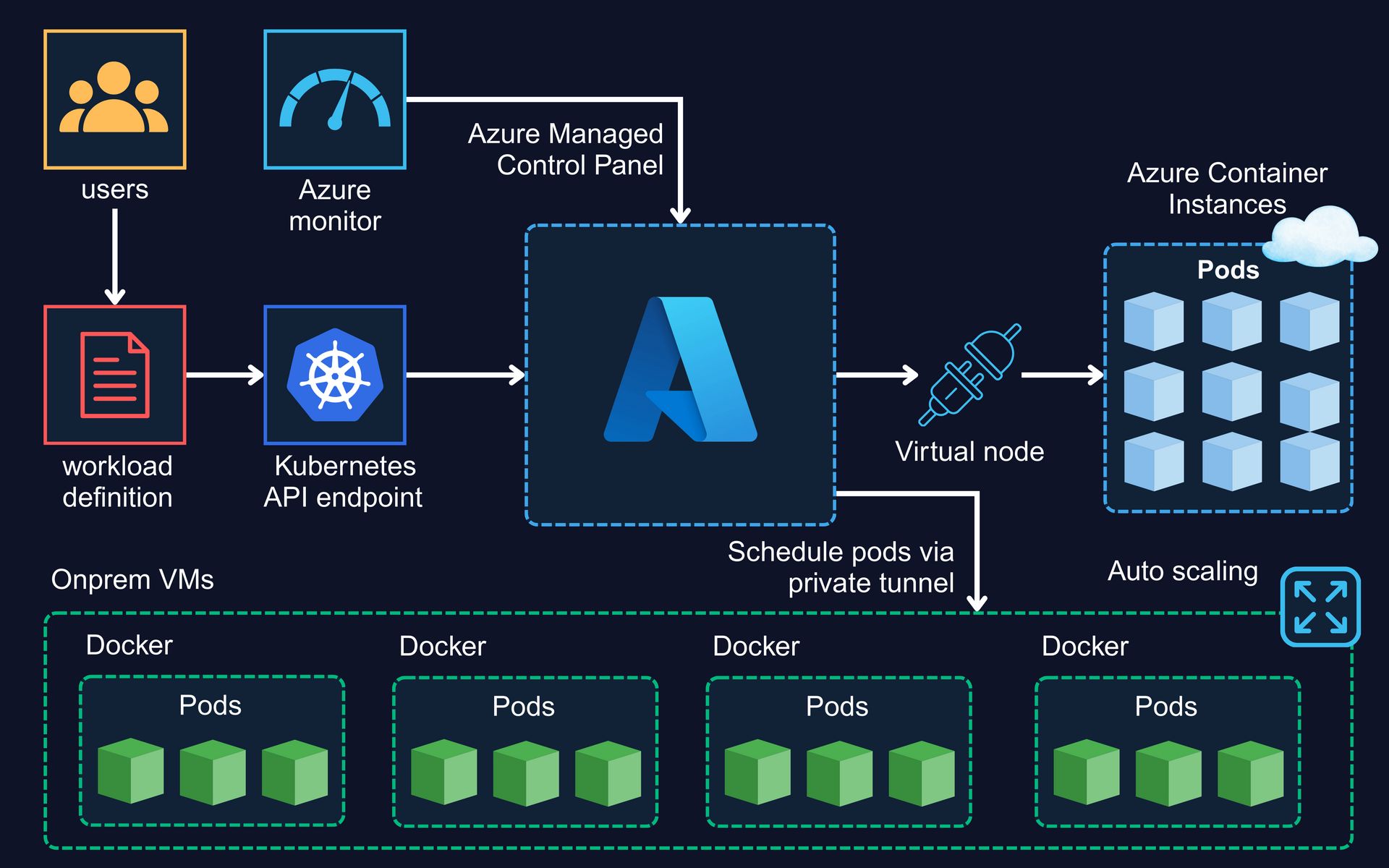
At the same time, workload execution becomes flexible. Pods can run on traditional VM backed node pools. Pods can also run on Azure Container Instances using virtual nodes.
Both are valid Kubernetes targets. Both accept the same workload definitions. But they do not share the same security characteristics.
Why pods running in two places matters
This is the most commonly misunderstood part of AKS security.
VM backed nodes
Long lived infrastructure
Full node level responsibility
OS hardening still matters
Network policies behave predictably
ACI backed pods
No customer managed VMs
No node access or SSH
Different networking behavior
Designed for burst workloads
Understanding this distinction is critical before designing security controls.
With this execution model clearly understood, we can now design security guardrails that are enforceable, unavoidable, and aligned with how AKS actually works in production.
🔴 Get my DevOps & Kubernetes ebooks! (free for Premium Club and Personal Tier newsletter subscribers)
Upgrade to Paid to read the rest.
Become a paying subscriber to get access to this post and other subscriber-only content.
UpgradePaid subscriptions get you:
- Access to archive of 250+ use cases
- Deep Dive use case editions (Thursdays and Saturdays)
- Access to Private Discord Community
- Invitations to monthly Zoom calls for use case discussions and industry leaders meetups
- Quarterly 1:1 'Ask Me Anything' power session




