TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case and remote job opportunities.
👋 Before we begin... a big thank you to today's sponsor PERFECTSCALE
[Kubernetes Workshop] In this workshop, Chimbu Chinnadurai (DoiT) and Anton Weiss (PerfectScale) will show how GKE’s Node Auto-Provisioning (NAP) with Compute Classes can:
→ Dynamically create node pools
→ Match the right machine types to your workloads
→ Reduce waste and cost
If you’re not a subscriber, here’s what you missed last week.
To receive all the full articles and support TechOps Examples, consider subscribing:
IN TODAY'S EDITION
🧠 Use Case
How OAuth Works
🚀 Top News
👀 Remote Jobs
Raiku is hiring a Infrastructure & DevOps Engineer
Remote Location: Worldwide
Auros is hiring a Senior Site Reliability Engineer
Remote Location: UK, Americas or Europe
📚 Resources
🛠 TOOL OF THE DAY
terracognita - Convert Cloud Infrastructure to Terraform Code.
Reads from existing public and private cloud providers (reverse Terraform) and generates your infrastructure as code on Terraform configuration
🧠 USE CASE
How OAuth Works
If you’ve ever:
Set up GitHub Actions to push artifacts to DockerHub or Google Container Registry
Connected Terraform Cloud to GitHub or GitLab for repository access
Used AWS Cognito or Azure AD (now Entra) to authenticate users into an internal dashboard
You’ve already touched OAuth. And probably didn’t even realize it. It shows up silently when APIs need to talk securely, when dashboards require login, or when CI/CD pipelines integrate with other tools.
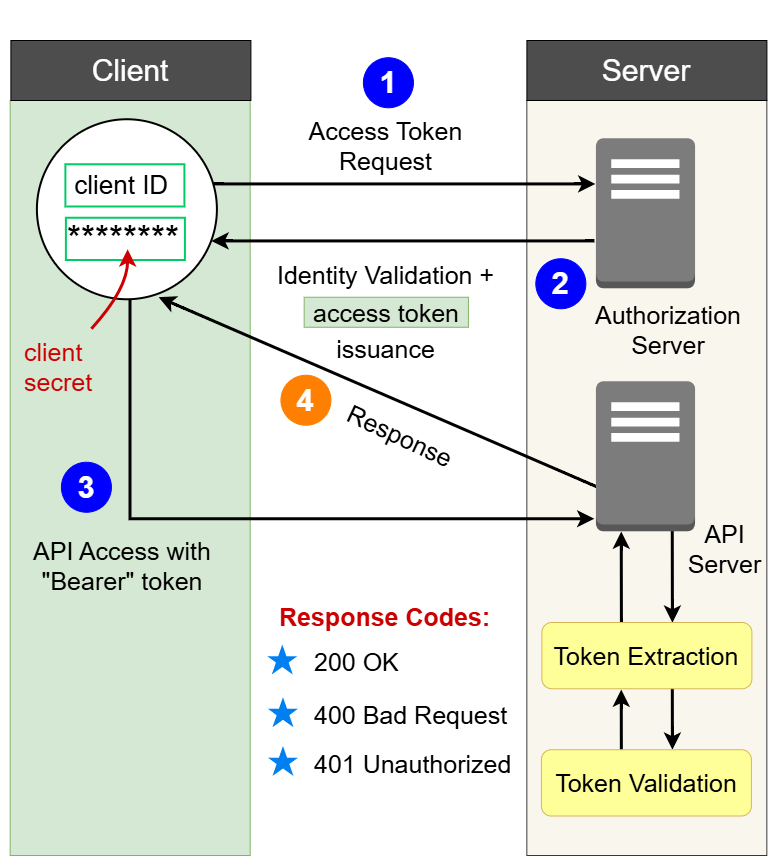
OAuth Workflow
1. Access Token Request
You configure your CI/CD pipeline, internal app, or automation tool to connect to an external system say, GitHub, Azure Vault, or a container registry.
The client (your app or tool) sends a request to the authorization server (e.g., GitHub OAuth server, Azure AD) with: client_id, client_secret, scope (optional), grant_type (e.g., client credentials)
This is the tool saying: “Here’s who I am. Can I get access to perform a task?”
2. Identity Validation and Token Issuance
The authorization server checks the credentials. If valid, it issues an access token.
This is not a password or a user credential. It’s a signed string representing what the client is allowed to do.
For example, GitHub may return a token that allows a GitHub Action to read and write to a repo.
3. Using the Access Token (Bearer Token)
Now, the client uses the token to hit protected APIs. Each call includes:
Authorization: Bearer <access_token>
The receiving API server extracts the token, validates it using keys from the identity provider, and checks claims like expiration and audience.
4. API Response
The server responds based on the validity of the token:
200 OKif the token is valid400 Bad Requestfor missing or malformed token401 Unauthorizedfor expired or invalid token
If your pipeline breaks, your login fails, or your API call gets rejected, start by asking: Was there a token involved? If yes, trace it back through the OAuth flow.
That's where most of the answers lie.
We are bringing a live workshop on GKE’s Node Auto-Provisioning (NAP) featuring Chimbu Chinnadurai (Senior Cloud Architect - DoiT) and Anton Weiss (Chief Cluster Whisperer - PerfectScale)
Looking to promote your company, product, service, or event to 46,000+ Cloud Native Professionals? Let's work together.