TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities, and articles.
👋 👋 A big thank you to today's sponsor UDACITY
Build real AI and tech skills, faster
Udacity helps you build the AI and tech skills employers actually need—fast. Learn from industry experts through hands-on projects designed to mirror real-world work, not just theory.
Whether you’re advancing in your current role or preparing for what’s next, Udacity’s flexible, fully online courses let you learn on your schedule and apply new skills immediately. From AI and machine learning to data, programming, and cloud technologies, you’ll gain practical experience you can show, not just list on a résumé.
Build confidence, stay competitive, and move your career forward with AI and tech skills that are in demand.
👀 Remote Jobs
Raiku is hiring a Infrastructure & DevOps Engineer
Remote Location: Worldwide
Pythian is hiring a Site Reliability Engineer
Remote Location: India
📚 Resources
Looking to promote your company, product, service, or event to 58,000+ Cloud Native Professionals? Let's work together. Advertise With Us
🧠 DEEP DIVE USE CASE
How Istio Ambient Mode Secures Kubernetes Traffic Without Sidecars
Service to service security in Kubernetes has traditionally relied on the sidecar model. Every Pod gets an extra proxy container, and all traffic is forced through it. The goal is simple:
Encrypt service-to-service traffic
Authenticate workloads
Enforce policy consistently
Observe traffic without changing application code
The problem is not intent. The problem is where that responsibility lives.
Sidecar Containers Basics
A sidecar container is a helper process that runs alongside the main application inside the same Pod.

The application focuses on core tasks. Handling requests, executing business logic, and responding to clients.
The sidecar focuses on peripheral tasks. Logging, metrics collection, security, traffic interception, or protocol handling.
Both containers share the same Pod boundary. They run on the same node, share the same network namespace, and can communicate through shared volumes.
From the application’s point of view, nothing changes. It continues to send and receive traffic as usual.
From the platform’s point of view, additional capabilities are now attached to the workload without modifying the application itself.
The key idea is separation of concerns at the container level, not at the service level.
The application does not know the sidecar exists. The sidecar exists to make the application easier to operate.
Kubernetes Sidecar Architecture
When sidecars are used at scale, they stop being a Pod level concern and become a cluster level architecture.
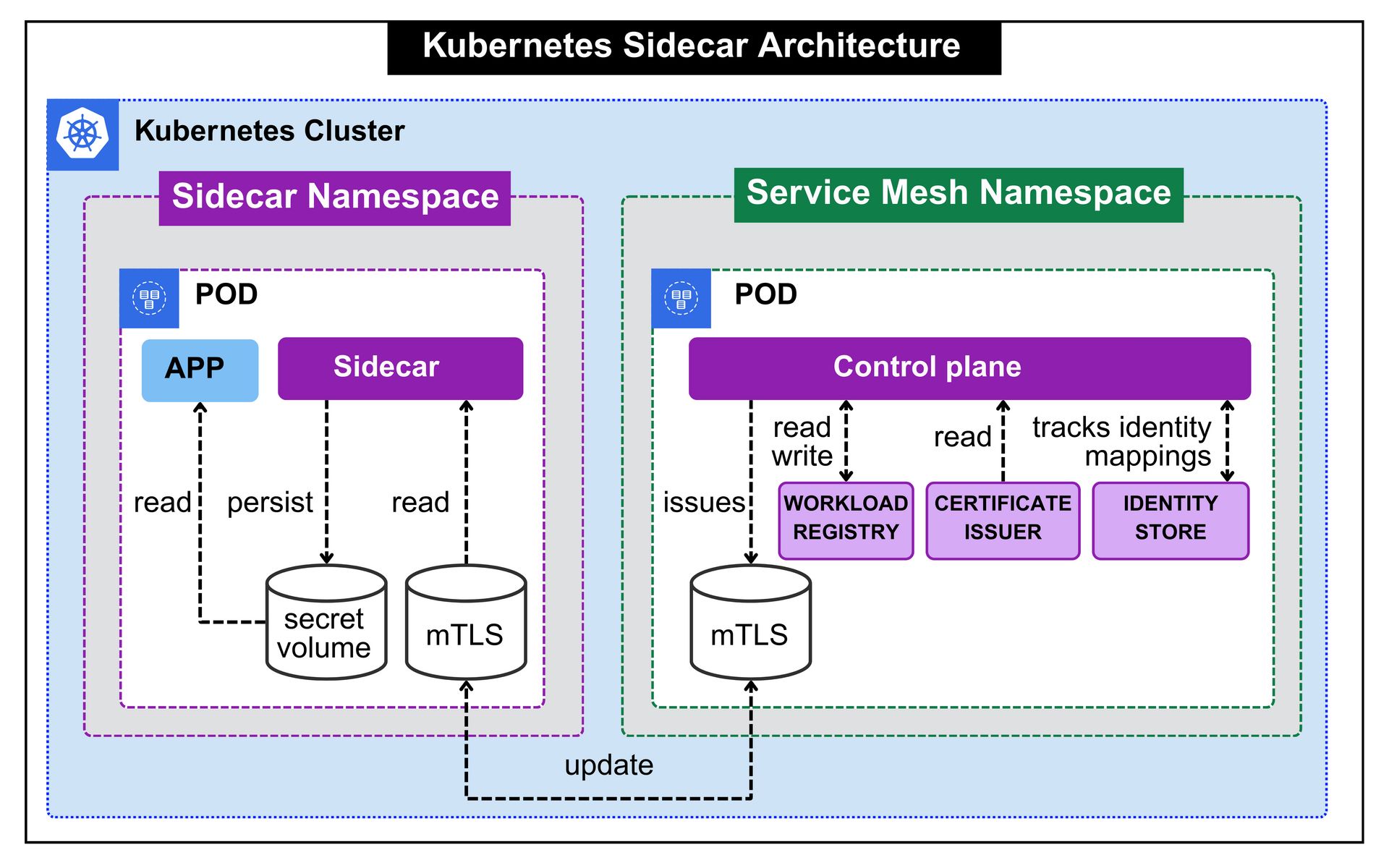
Each application Pod runs its own sidecar proxy. That proxy depends on a centralized control plane for identity, certificates, and policy updates.
The control plane maintains a registry of workloads, issues certificates, tracks identity mappings, and pushes configuration changes continuously. Sidecars read secrets and mTLS material from mounted volumes and use them to secure traffic between services.
Every workload now includes infrastructure logic as part of its runtime footprint.
Certificates are rotated per Pod.
Configuration updates are pushed per proxy.
Failures and restarts happen at the Pod boundary.
The architecture works because everything is explicit and tightly coupled. But that coupling is also the cost.
As the number of Pods increases, the number of proxies increases with it. Security scales linearly, but so does resource consumption, operational complexity, and blast radius.
The mesh becomes reliable, but heavier with every workload added.
Having established the fundamentals of how sidecar based service meshes work, let’s now dive into the architecture and finer details of how traffic security is implemented in Kubernetes.
Service Mesh With Sidecar Workflow
Istio Ambient Mode Architecture
🔴 Get my DevOps & Kubernetes ebooks! (free for Premium Club and Personal Tier newsletter subscribers)
Upgrade to Paid to read the rest.
Become a paying subscriber to get access to this post and other subscriber-only content.
UpgradePaid subscriptions get you:
- Access to archive of 250+ use cases
- Deep Dive use case editions (Thursdays and Saturdays)
- Access to Private Discord Community
- Invitations to monthly Zoom calls for use case discussions and industry leaders meetups
- Quarterly 1:1 'Ask Me Anything' power session




