TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities and articles.
👋 Before we begin... a big thank you to today's sponsor ZESTY
Still optimizing Kubernetes costs manually?
It’s time to automate.
Transition confidently from reactive dashboards and scripts to scalable, hands-free Kubernetes optimization with Zesty's playbook.
In this playbook, you will learn how to:
Spot the hidden costs of manual Kubernetes optimization
Shift from dashboards and scripts to smart, automated workflows
Evaluate your current maturity for automation
Build a roadmap to hands-free, scalable cost optimization
This playbook shares real-world examples and actionable strategies to run Kubernetes leaner, faster, and more efficiently.
If you’re not a subscriber, here’s what you missed last week.
To receive all the full articles and support TechOps Examples, consider subscribing:
IN TODAY'S EDITION
🧠 Use Case
DevSecOps with Terraform and CICD Pipelines
👀 Remote Jobs
Avalanche is hiring a DevOps Engineer
Remote Location: Worldwide
Trust Wallet is hiring a Senior Mobile DevOps Engineer
Remote Location: Worldwide
📚 Resources
🧠 USE CASE
DevSecOps with Terraform and CICD Pipelines
The more I see terraform code written, maintained and deployed I sense it isn't treated as an app codebase, terraform is just for automating the provisioning isn’t it? This is the generic mindset. Once for all, it is beyond that…
The real impact shows up in how security attention shifts. A misconfigured IAM role or open security group found early is nearly 100X impactful to fix than the same in production. With DevSecOps + Terraform and CI/CD pipelines, that difference is the line between a secure release and a costly breach. Here is the visual illustration of the context.
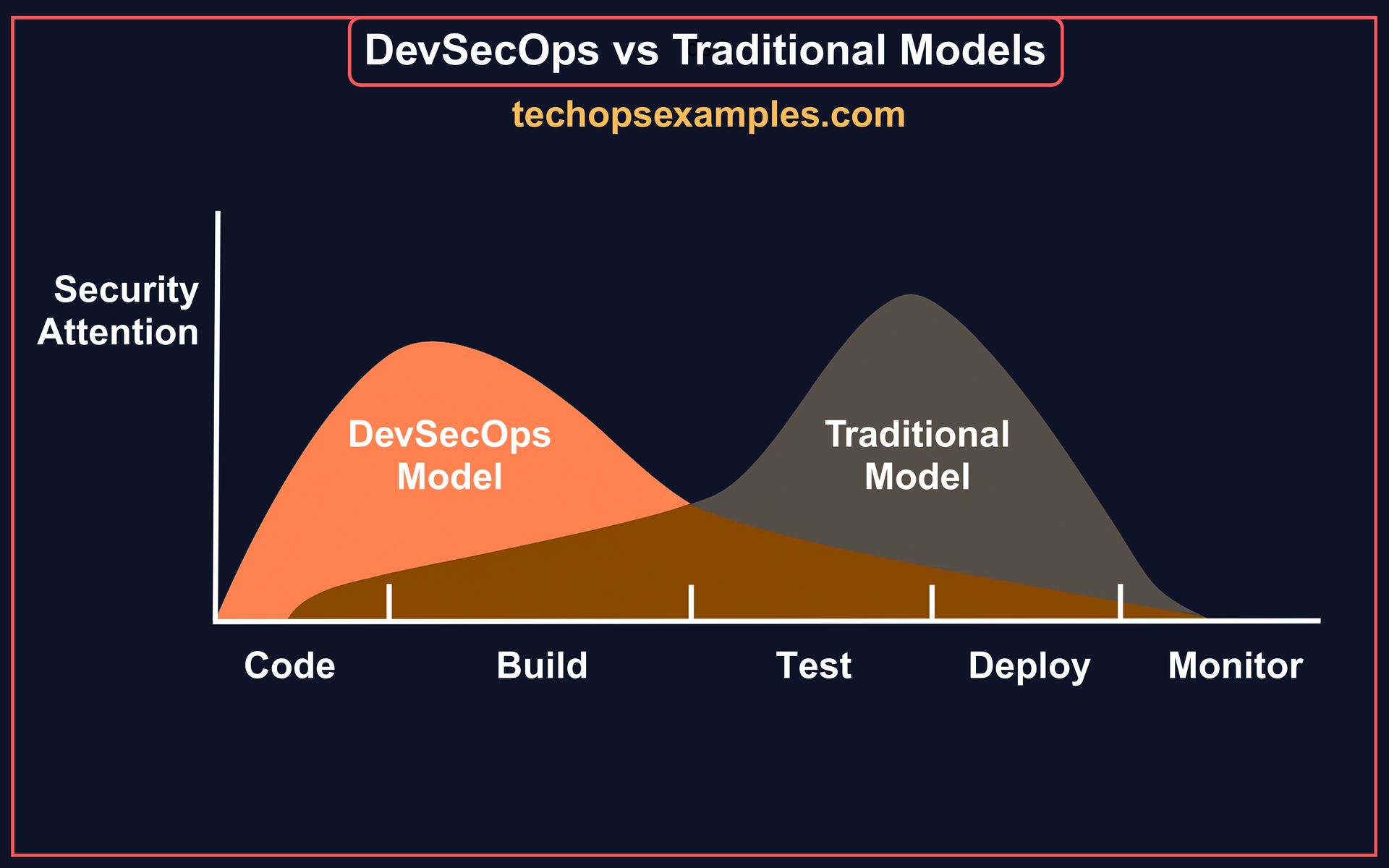
Architecture In Action
A typical architecture looks like the depiction below. Most teams wire in scans and stop there. The real value comes when you go deeper.

1. Code as the First Security Layer
Enforce pull request checks for
tflint,tfsec,checkov.Block merges if secrets or hard coded credentials appear.
Require plan reviews before apply, treat infra changes like app changes.
2. Pipeline Security Hardening
Run Terraform in isolated runners with least privilege IAM roles.
Lock and encrypt state in S3 or GCS buckets with restricted access.
Pin Terraform and provider versions in pipelines to avoid breaking or malicious updates.
3. Test Beyond Unit
Run ephemeral environment deployments in pipelines for high risk infra changes.
4. Deployment Guardrails
Apply compliance controls inline (CIS benchmarks, tagging, encryption).
Auto fail applies that drift from baseline policies.
5. Continuous Monitoring
Automate drift detection and trigger corrective pipelines, not manual fixes.
Feed runtime cloud misconfig alerts back into Terraform repos to keep infra in sync.
🔴 Get my DevOps & Kubernetes ebooks! (free for Premium Club and Personal Tier newsletter subscribers)
Looking to promote your company, product, service, or event to 52,000+ Cloud Native Professionals? Let's work together.



