TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities and articles.
👋 Before we begin, I’m happy to partner with O’Reilly and PerfectScale to bring you a practical FinOps guide for cloud practitioners.
Get FinOps insights from 10,000+ cloud practitioners.
In this free 450+ pages of expert FinOps guide, you’ll learn how to:
- Forecast cloud spend with accuracy
- Build a culture of accountability across teams
- Automate repetitive cost tasks
- Use unit economics for data-driven decisions
Limited time only.
IN TODAY'S EDITION
🧠 Use Case
Common Docker Misconfigurations and How to Prevent Them
👀 Remote Jobs
Ampa is hiring a IT Infrastructure Engineer
Remote Location: Worldwide
3Pillar is hiring a Senior DevOps Engineer- AWS
Remote Location: India
📚 Resources
👋 Before we begin... a big thank you to today's sponsor DEX AI
Dex AI Scrapes the internet and sets up interviews for you
Dex is a conversational AI and career matchmaker that works on behalf of each person. You spend 15-20 minutes on the phone with him, talking about your experience, your ambitions and your non-negotiables.
Dex then scans thousands of roles and companies to identify the most interesting and compatible opportunities.
Once we’ve found a match, Dex connects you to hiring managers and even helps you prep for interviews.
Thousands of exceptional engineers have already signed up and we’re partnered with many of the UK’s leading Start-ups, Scale-ups, hedge funds and tech companies.
Don’t waste another day at a job you hate. Speak with Dex today.
🧠 USE CASE
Common Docker Misconfigurations and How to Prevent Them
DevOps engineers often find themselves chasing problems in Docker that turn out to be simple misconfigurations. A missing limit, an overlooked flag, or an insecure default can lead to wasted hours in debugging, performance degradation, or even security incidents. Most of these challenges are avoidable if the basics are set right from the start.
It is worth taking a quick look at how Docker works before we get into the core of today's topic.

A typical Docker workflow starts with the client running commands like docker build, docker pull, or docker run. These commands are sent to the Docker daemon on the host. The daemon fetches images from a registry or builds them locally, stores them as reusable artifacts, and then launches containers from those images. Containers are the isolated environments where applications actually run.
Typical Misconfigurations You Should Avoid:
1. Running Docker container in rootless mode

By default, Docker containers run as the root user, which increases the risk of privilege escalation if the container is compromised. A safer practice is to create and use a non root user inside the container.

2. Using tagged minimal base images and multistage builds

Using large untagged images leads to bloated containers and unpredictable builds. A better approach is to use versioned tags and multistage builds. Here, dependencies are installed in a builder image, and only the required artifacts are copied into a lightweight runtime image.

3. Using COPY command with specific parameters

Using a broad COPY . . can unintentionally include unnecessary files such as configs, build artifacts, or secrets. It makes images larger and riskier. Instead, copy only the required files or directories explicitly, like COPY target/app.jar /app.

4. Update and install packages in the same RUN instruction
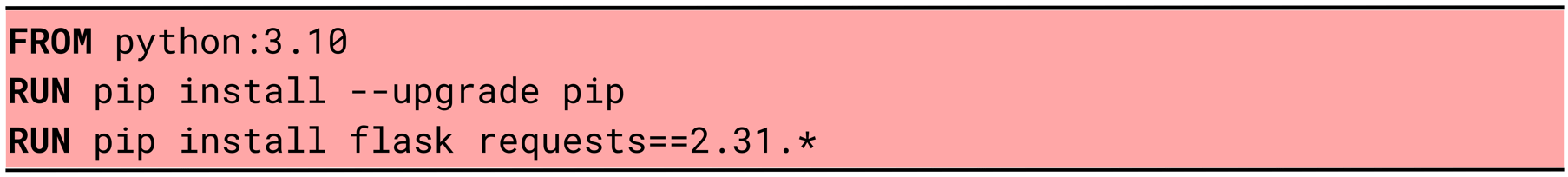
Splitting updates and package installations across multiple RUN layers leads to larger image sizes and cache inconsistencies. Combining them in a single RUN reduces layers, keeps images cleaner, and ensures package versions remain consistent during builds.

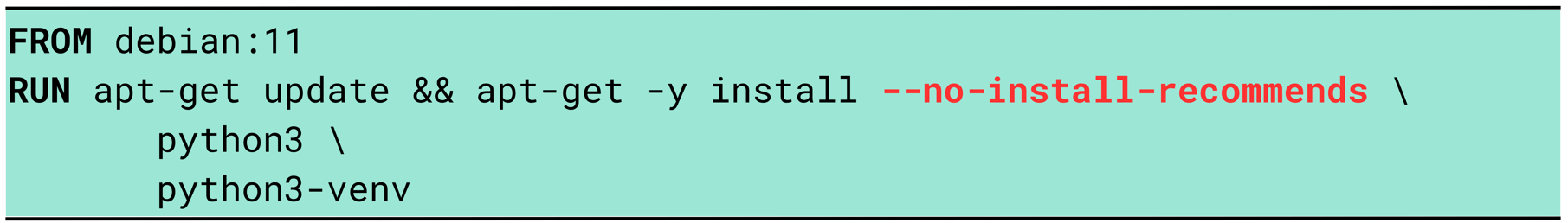
5. Removing unnecessary dependencies
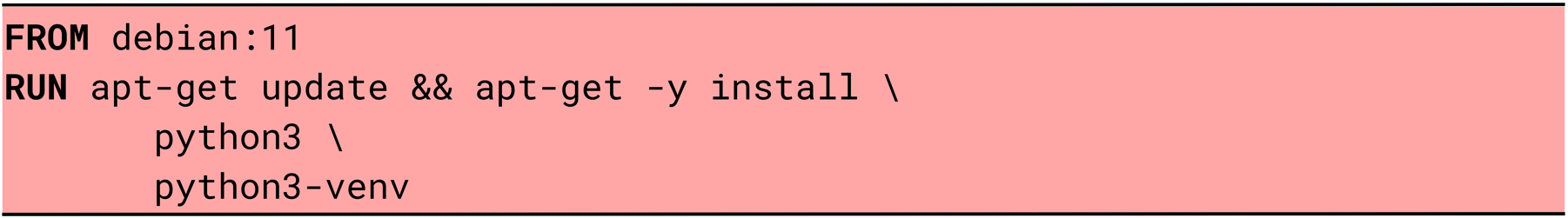
Package managers often install extra packages by default, which makes images larger and more complex. Installing only what is strictly required keeps the image lightweight, improves maintainability, and reduces the potential attack surface.
Takeaway
Write Dockerfiles with least privilege, minimal images, explicit copies, single layer installs, and trimmed dependencies to achieve smaller, safer, and more predictable containers.
🔴 Get my DevOps & Kubernetes ebooks! (free for Premium Club and Personal Tier newsletter subscribers)
Looking to promote your company, product, service, or event to 54,000+ DevOps and Cloud Professionals? Let's work together.




