TechOps Examples
Hey — It's Govardhana MK 👋
Along with a use case deep dive, we identify the remote job opportunities, top news, tools, and articles in the TechOps industry.
IN TODAY'S EDITION
🧠 Use Case
AWS VPC Peering Overview
🚀 Top News
👀 Remote Jobs
Dedalus HealthCare is hiring a Cloud Architect
Remote Location: India, Germany, Italy, France
SUSE is hiring a Principal SaaS Observability & DevOps Engineer
Remote Location: India, Czechia, Bulgaria, Brazil, Netherlands, Portugal, Spain, Taiwan
📚 Resources
📢 Reddit Threads
🛠 TOOL OF THE DAY
SecTemplates - Open source templates you can use to bootstrap your security programs.
Incident Response Program Pack
Security Exceptions program pack
Vulnerability Management Program Pack
External Penetration Testing Program Pack
🧠 USE CASE
AWS VPC Peering Overview
The scenarios where VPC peering is used vary, but here are some real world cases based on my experience:
You have multiple AWS accounts and need direct network connectivity between VPCs.
Your organization has separate environments (Dev, Staging, Prod) in different VPCs and wants low latency private communication between them.
You’re integrating with a partner’s AWS infrastructure without exposing services over the public internet.
You need to enable cross-region communication between workloads without relying on VPN or Transit Gateway.
To begin with…
What is VPC Peering ?
It is a direct, private network connection between two VPCs.
Think of it as an agreement where both VPCs decide to trust each other and allow direct traffic.
It doesn’t rely on an intermediary like AWS Transit Gateway or a VPN.
Once a peering connection is established, the two VPCs can talk to each other via their private IPs, provided the right route tables and security group rules are in place.
Here, I’ve simplified how it works:

Once this is done, traffic flows between the VPCs privately and securely, without leaving AWS’s backbone network.
VPC Peering Architecture
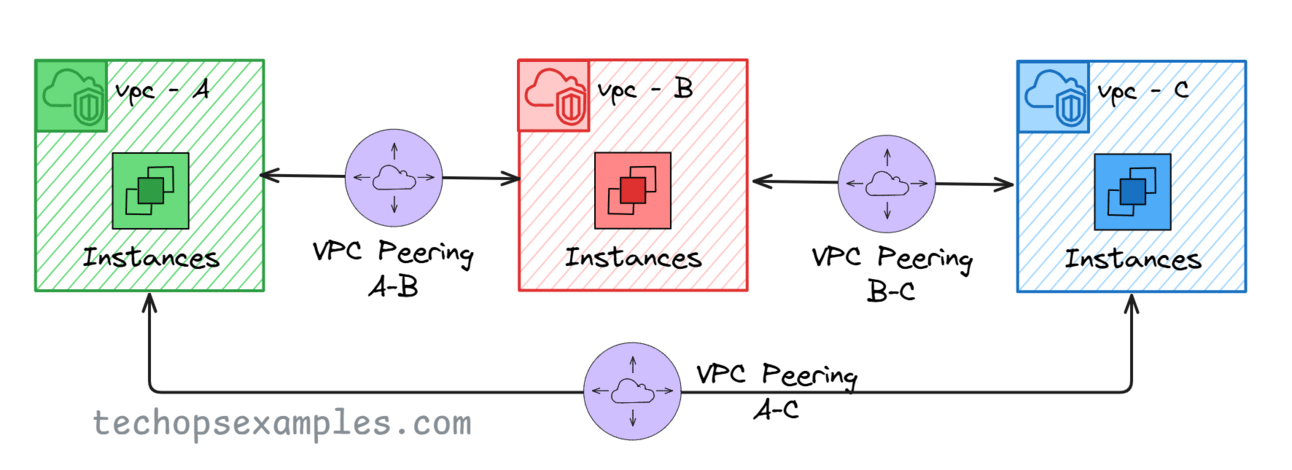
VPC peering follows a full mesh architecture, meaning every VPC must have a direct peering connection with every other VPC it needs to communicate with.
In this Example:
VPC A ↔ VPC B (Peered)
VPC B ↔ VPC C (Peered)
VPC A ↔ VPC C (Peered)
Notice that even though A is connected to B, and B is connected to C, traffic cannot flow from A to C through B.
If you need A to talk to C, you must set up a separate peering connection.
Note: This can get complex when dealing with multiple VPCs.
For further reading: Common VPC peering connection configurations
Things to Consider
While VPC peering is a simple and cost effective solution for interconnecting VPCs, it isn’t free from limitations:
Each VPC must be explicitly peered.
You have to update route tables manually; there’s no automatic propagation like in Transit Gateway.
Security Groups & NACLs to be adjusted to allow traffic between VPCs.
Intra region peering is free, but cross region peering incurs data transfer charges.
VPCs cannot be peered if they have overlapping IP address ranges.
Use VPC peering when you need low latency, private connectivity between two VPCs with predictable network paths.
However, if you’re dealing with a many-to-many network architecture, AWS Transit Gateway is often a better option as it simplifies connectivity.
If you just need to expose specific services across VPCs without full network connectivity, AWS PrivateLink might be a more secure and scalable alternative.
You may even like:
Looking to promote your company, product, service, or event to 38,000+ Cloud Native Professionals? Let's work together.

