TechOps Examples
Hey — It's Govardhana MK 👋
Welcome to another technical edition.
Every Tuesday – You’ll receive a free edition with a byte-size use case, remote job opportunities, top news, tools, and articles.
Every Thursday and Saturday – You’ll receive a special edition with a deep dive use case, remote job opportunities, and articles.
👋 Before we begin... a big thank you to today's sponsor FELLOW
You wouldn’t allow unmanaged devices on your network, so why allow unmanaged AI into your meetings?
Shadow IT is becoming one of the biggest blind spots in cybersecurity.
Employees are adopting AI notetakers without oversight, creating ungoverned data trails that can include confidential conversations and sensitive IP.
Don't wait until it's too late.
This Shadow IT prevention guide from Fellow.ai gives Security and IT leaders a playbook to prevent shadow AI, reduce data exposure, and enforce safe AI adoption, without slowing down innovation.
It includes a checklist, policy templates, and internal comms examples you can use today.
👀 Remote Jobs
Iodine is hiring a Site Reliability Engineer - AWS
Remote Location: Worldwide
Toogeza is hiring a Platform/DevOps Engineer
Remote Location: Worldwide
📚 Resources
Looking to promote your company, product, service, or event to 55,000+ Cloud Native Professionals? Let's work together. Advertise With Us
🧠 DEEP DIVE USE CASE
Step-by-Step Guide to AWS S3 Object Encryption
Misconfigured S3 buckets are a leading cause of data leaks in the cloud. Public access settings often expose private information to the internet, costing companies millions and damaging customer trust. Can’t believe?
Here's a short list of incidents involving S3 hacks.
Before jumping into storage level protections, let us first understand how encryption works in simple terms.

Data is locked using one key and unlocked using another. The public key is used to lock the data. The secret key is used to unlock it. Without the secret key, no one can read the data. This is the basic idea behind how most secure systems protect information.
Amazon S3 supports multiple options to encrypt objects at rest, but it's important to note that S3 does not encrypt your data by default. You have to choose and configure the encryption method that fits your needs. Before choosing, ask yourself:
Who encrypts the data?
Where is the key stored?
Who manages the key?
Here are the four methods available for encrypting objects in S3: SSE-S3, SSE-KMS, SSE-C, Client Side Encryption
1. SSE-S3
This is the easiest way to get encryption at rest with zero code changes.
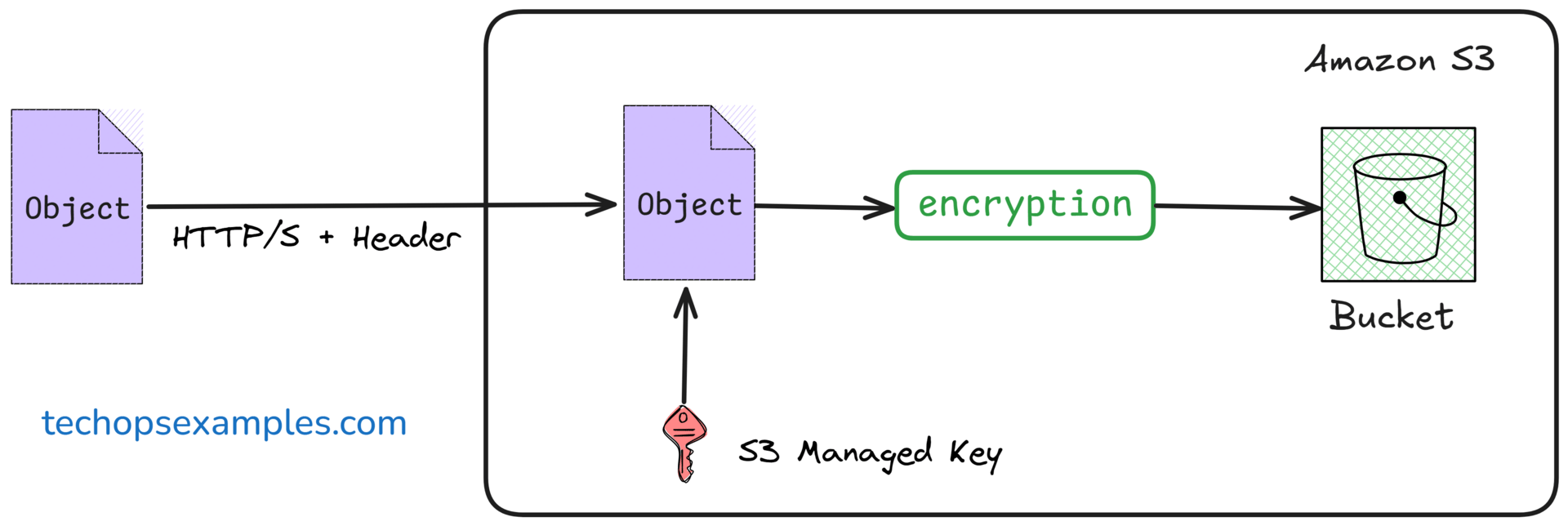
Encrypts your objects using AES-256 automatically during upload.
Decrypts them transparently during download.
All keys are fully managed by AWS. You don’t create, rotate, or store anything.
You can enable SSE-S3 in two ways:
1. Per object: Use this header when uploading
x-amz-server-side-encryption: AES2562. Bucket wide default:
Go to S3 > Bucket > Properties > Default Encryption, and choose AES-256.
This ensures all uploads to the bucket are encrypted without requiring any headers from clients.
What to watch out for:
Since AWS owns the keys, you won’t get CloudTrail events for key access.
You cannot define key rotation intervals or custom key policies.
Default encryption helps, but old objects uploaded before enabling it remain unencrypted.
Use S3 Inventory Reports to confirm which objects are encrypted.
2. SSE-KMS
SSE-KMS builds on top of SSE-S3 but gives you more control over key management and access monitoring.

Uses AWS KMS to manage encryption keys.
Encrypts objects with a unique data key, which is itself protected by a Customer Master Key (CMK) in KMS.
Decryption requires permissions not just to the S3 object but also to the KMS key.
You can enable SSE-KMS in two ways:
1. Per object: Add this header when uploading:
x-amz-server-side-encryption: aws:kms2. Bucket wide default:
Under S3 > Bucket > Properties > Default Encryption, choose AWS Key Management Service key (SSE-KMS) and select a KMS key (either AWS-managed or customer-managed).
What you can control:
You can create, name, and define key policies for each key.
You can let AWS auto rotate keys annually or manually rotate them yourself.
Each encryption and decryption action is logged in AWS CloudTrail, including who accessed what and when.
If a user has S3 access but lacks kms:Decrypt on the KMS key, the download will fail.
I am giving away 50% OFF on all annual plans of membership offerings for a limited time.
A membership will unlock access to read these deep dive editions on Thursdays and Saturdays.
Upgrade to Paid to read the rest.
Become a paying subscriber to get access to this post and other subscriber-only content.
UpgradePaid subscriptions get you:
- Access to archive of 200+ use cases
- Deep Dive use case editions (Thursdays and Saturdays)
- Access to Private Discord Community
- Invitations to monthly Zoom calls for use case discussions and industry leaders meetups
- Quarterly 1:1 'Ask Me Anything' power session




